Monday, January 4, 2010
how secure of your apache server???
- Nikto v2.1.0/2.1.0
---------------------------------------------------------------------------
+ Target IP: 192.168.1.15
+ Target Hostname: 192.168.1.15
+ Target Port: 80
+ Start Time: 2009-11-23 0:02:00
---------------------------------------------------------------------------
+ Server: Apache/2.2.13 (Fedora)
+ OSVDB-0: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-0: Apache/2.2.13 appears to be outdated (current is at least Apache/2.2.14). Apache 1.3.41 and 2.0.63 are also current.
+ OSVDB-3268: /icons/: Directory indexing is enabled: /icons
+ OSVDB-3233: /icons/README: Apache default file found.
+ 3582 items checked: 5 item(s) reported on remote host
+ End Time: 2009-11-23 0:02:00 (18 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
========== after mod_security installed ===========================
[root@manutd nikto-2.1.0]# ./nikto.pl -C all -host 192.168.1.15
- Nikto v2.1.0/2.1.0
---------------------------------------------------------------------------
+ Target IP: 192.168.1.15
+ Target Hostname: 192.168.1.15
+ Target Port: 80
+ Start Time: 2009-11-23 0:08:00
---------------------------------------------------------------------------
+ Server: Apache/2.2.0 (Fedora)
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-0: Apache/2.2.0 appears to be outdated (current is at least Apache/2.2.14). Apache 1.3.41 and 2.0.63 are also current.
+ 3582 items checked: 2 item(s) reported on remote host
+ End Time: 2009-11-23 0:09:00 (55 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
======== after apache config tuned ===============
[root@manutd nikto-2.1.0]# ./nikto.pl -C all -host 192.168.1.15
- Nikto v2.1.0/2.1.0
---------------------------------------------------------------------------
+ Target IP: 192.168.1.15
+ Target Hostname: 192.168.1.15
+ Target Port: 80
+ Start Time: 2009-11-23 0:22:00
---------------------------------------------------------------------------
+ Server: Apache
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ 3582 items checked: 1 item(s) reported on remote host
+ End Time: 2009-11-23 0:23:00 (57 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
========== last modification =============
[root@devil nikto-2.1.0]# ./nikto.pl -C all -host 192.168.1.15
- Nikto v2.1.0/2.1.0
---------------------------------------------------------------------------
+ Target IP: 192.168.1.15
+ Target Hostname: 192.168.1.15
+ Target Port: 80
+ Start Time: 2009-11-23 0:57:00
---------------------------------------------------------------------------
+ Server: This is Windows IIS 10. Enjoy hacking
+ 3582 items checked: 0 item(s) reported on remote host
+ End Time: 2009-11-23 0:58:00 (45 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
see , Windows IIS 10, Enjoy Hacking :P
Intruders cant guess what is my server platform, but they still can grab my webpage header.
Maybe they can guess from my webpage header.
see, nothing to be found.... i just do a basic modification in apache and mod_security.
For more advance topics in mod_security, please read below 2 books. It is very useful for apache
Apache Security by Ivan Ristic
The Definitive Guide to Apache mod_rewrite by Rich Bowen
Actually i have to do more advance web vulnerable testing because tested with 1 tools is not enough. It is dangerous if the production server only done with 1 tools for pen test.
hopefully i got time to do more advance pentest with various open source web scanner also proprietary product like NESSUS
Pentoo, another security distro
i had tested with my EEEPC 1005HA, it is very fast compared to BT4. Of coz BT4 is slower due to the x windows client is KDE3.x.
There's 2 things really impressed me which are latest kernel 2.6.32 and 2x CUDA Apps. The advantages of new kernel is more driver supported and i can use EXT4, i like this File System pretty much due to better performance. Yet, the CUDA Apps really make use the processing speed of CUDA, it is really good in brute force.
There's a GUI thingy called Fast Track Web Interface to allow people who are not familiar with linux have better life to play with this tools. This kind of GUI thingy also available in other security distro like NST.
I plan to install the Pentoo in my eeepc ,but my china friend ask me to wait for BT4 due to Bt4 final will release in this month. As i see from current development, the BT4 will come with Kernel 2.6.29 and my eeepc wireless card is able to detected automatically. I can install it thru source code but look like not so PERFECT already.
Well, let see what happen in BT4 after release.
Please see the Pentoo screenshot which i took by vmware


Sunday, January 3, 2010
1st blog of 2010 - CUDA enabled GPGPU
As we know the brute force attack is required high speed processing power in order to achieve it.
but nowadays brute force attack can be done a normal home use PC. Thanks to NVIDIA who make the CUDA chipset to speed up the calculation of processing speed.
1 years ago, i dont see many of the CUDA based applications available in internet. With the effort of programmers, they had done some CUDA apps for brute force which is available in BackTrack 4 and Pentoo security distro.
Recently, ASUS has announced their home made super computer which is powered by CUDA GPGPU. It is very cheap like 200-300 USD per teraflops
As we can see, more and more CUDA based applications will be available soon. It is good because the calculation speed is speed up and the price is lower down whereas It is bad for people who have evil mindset.
Nothing to be safe if CUDA really make use in the our life. Any crypto can be decrypt within very few minutes or less.
Tuesday, June 9, 2009
server compromised - finding the intruder
Ask my favor to do some checking.
according to him, the intruder left 3 files into one of the web directory.
2 is text files and another 1 is an application.
i had check these 2 text files which are harmless code and the application is eggdrop which is IRC Bot application.
since i know it is eggdrop, i see where the files has been installed.
[root@www ~]# find / -name egg*
/var/www/html/crew/libraries/x/conf/eggdrop.chan
/var/www/html/crew/libraries/x/doc/html/egg-core.html
/var/www/html/crew/libraries/x/doc/man1/eggdrop.1
/var/www/html/crew/libraries/x/doc/eggdrop.doc
/var/www/html/crew/libraries/x/eggdrop-1.6.6
/var/www/html/crew/libraries/x/logs/eggdrop.log.20090608
/var/www/html/crew/libraries/x/logs/eggdrop.log.20090606
/var/www/html/crew/libraries/x/logs/eggdrop.log.20090607
/var/www/html/crew/libraries/x/logs/eggdrop.log.20090609
/usr/share/pixmaps/gnobots2/eggs.png
/usr/lib/python2.4/site-packages/gtk-2.0/egg
from the result result i found out the application installed on /var/www/html/crew/libraries/
Now, see when the application install on the server
[root@www ~]# ls -la /var/www/html/crew/libraries/
-rwxr-xr-x 1 loon loon 16091 Nov 8 2008 unzip.lib.php
-rwxr-xr-x 1 loon loon 6512 Nov 8 2008 url_generating.lib.php
drwxr-xr-x 10 loon loon 4096 Jun 9 19:32 x
-rw-r--r-- 1 loon loon 1868180 Jun 6 05:48 x.tar.gz
-rwxr-xr-x 1 loon loon 6486 Nov 8 2008 zip.lib.php
----- --------------- more ----------------------------------------
see the line with red color, hints is there.
Now, go further... look at /var/log/html/crew/libraries/x
[root@www x]# ls -la /var/www/html/crew/libraries/x
total 2536
drwxr-xr-x 10 loon loon 4096 Jun 9 19:32 .
drwxr-xr-x 11 loon loon 4096 Jun 6 05:48 ..
-rw-r--r-- 1 loon loon 0 Jun 9 22:23 av.db
-rw-r--r-- 1 loon loon 71820 Jun 9 22:12 bs_data.eggdrop
-rw-r--r-- 1 loon loon 71031 Jun 9 22:12 bs_data.eggdrop.bak
drwxr-xr-x 2 loon loon 4096 Jun 6 05:54 conf
-rw-r--r-- 1 loon loon 0 Aug 18 2006 cs_spam_word.conf
drwxr-xr-x 5 loon loon 4096 Apr 5 2007 doc
-rw-r--r-- 1 loon loon 1163288 Sep 6 2001 eggdrop-1.6.6
drwxr-xr-x 3 loon loon 4096 Apr 5 2007 filesys
drwxr-xr-x 4 loon loon 4096 Apr 5 2007 help
-rw-r--r-- 1 loon loon 0 Aug 18 2006 klines
drwxr-xr-x 2 loon loon 4096 Apr 5 2007 language
drwxr-xr-x 2 loon loon 4096 Jun 9 00:01 logs
-rw-r--r-- 1 loon loon 5 Jun 6 05:57 pid.eggthrone
-rw-r--r-- 1 loon loon 465 Aug 18 2006 run
drwxr-xr-x 2 loon loon 4096 Jun 6 05:49 scripts
-rw-r--r-- 1 loon loon 14368 Feb 25 2004 shade
drwxr-xr-x 2 loon loon 4096 Apr 5 2007 text
-rwxrwxrwx 1 loon loon 1163288 Sep 6 2001 x
-rw-r--r-- 1 loon loon 7745 Jun 6 05:49 x3
-rwxr-xr-x 1 loon loon 21516 May 30 2007 xh
see, most of them are 6th Jun 2009, i believe the application runs on that day. Yet, i also believe it is installed on the same day.
The IRC Bot are runing by both same user and group, loon. Then, i talk to the user and he said he didnt share his account with anyone.
let's see anyone inside the server or not
[root@www x]# w
20:03:13 up 167 days, 43 min, 4 users, load average: 0.00, 0.02, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
alex pts/2 118.100.121.74 17:51 2:10m 0.04s 0.03s sshd: alex [priv]
loon pts/3 60.52.19.122 17:54 1:06m 0.02s 0.02s -bash
alex pts/5 118.100.125.164 19:24 35:32 0.03s 0.01s sshd: alex [priv]
alex pts/6 118.100.125.164 19:30 0.00s 0.08s 0.01s sshd: alex [priv]
shit, someone inside and that user said he didnt login to the server. i believe this is intruder.
i do whois and see where this IP address came from
[root@www x]# whois 60.52.19.122
[Querying whois.apnic.net]
[whois.apnic.net]
% [whois.apnic.net node-2]
% Whois data copyright terms http://www.apnic.net/db/dbcopyright.html
inetnum: 60.48.0.0 - 60.54.255.255
netname: XDSLSTREAMYX
descr: Telekom Malaysia Berhad
descr: Network Strategy
descr: Wisma Telekom
descr: Jalan Pantai Baru
descr: 50672 Kuala Lumpur
country: MY
from the return result , seems like the user from TMNET users.
do the netstat to see what connection available now
[root@www x]# netstat -an|more
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:2208 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:804 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:6667 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:44526 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:10000 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:2207 0.0.0.0:* LISTEN
tcp 0 0 203.114.11.102:51646 194.14.236.50:6667 ESTABLISHED
tcp 0 0 203.114.11.102:55317 202.30.50.120:43 ESTABLISHED
tcp 0 0 :::8897 :::* LISTEN
--------------------------- more ---------------------------------------------------
see the line with red color, see the port 6667, which is IRC port.
now try whois that IP
[root@www x]# whois 194.14.236.50
[Querying whois.ripe.net]
[whois.ripe.net]
% This is the RIPE Whois query server #2.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: This output has been filtered.
% To receive output for a database update, use the "-B" flag
% Information related to '194.14.236.0 - 194.14.236.255'
inetnum: 194.14.236.0 - 194.14.236.255
netname: DALNET-2
descr: DALnet unrouted servers
remarks: ################################################
remarks: If you get scanned by 194.14.236.50 you are NOT
---------------------------- more ------------------------------------------------
it is dalnet server.
lol, The intruder must be malaysian because malaysian very very like dalnet IRC.
i'm one of them in N year ago.
go further to see the port 6667.
[root@www alex]# lsof -i tcp:6667
COMMAND PID USER FD TYPE DEVICE SIZE NODE NAME
x 2709 loon 6u IPv4 37479003 TCP 203.114.11.102:51646->pool.dal.net:ircd (ESTABLISHED)
lsof is coolz..
found out the PID is 2709 and user is loon.
that mean the x is executed by loon and PID is 2709.
application is x
now use ps command to see the x
[root@www ~]# ps auxww |grep x
root 409 0.0 0.0 0 0 ? S<>
mysql 1006 0.0 1.0 143508 21536 ? Sl Jan08 1:14 /usr/libexec/mysqld --basedir=/usr --datadir=/var/lib/mysql --user=mysql --pid-file=/var/run/mysqld/mysqld.pid --skip-external-locking --socket=/var/lib/mysql/mysql.sock
root 1565 0.0 0.0 6744 1772 ? Ss Jan08 0:14 /usr/libexec/postfix/master
postfix 1568 0.0 0.9 24980 19952 ? S Jan08 0:47 qmgr -l -t fifo -u
root 2308 0.0 0.0 1672 404 ? Ss 2008 0:00 klogd -x
loon 2709 0.0 0.2 8032 4152 ? S Jun06 0:01 -bash -m x3
root 7579 0.0 0.0 1900 376 ? Ss 2008 0:00 gpm -m /dev/input/mice -t exps2
root 7820 0.0 0.0 1752 448 ? S 2008 0:00 /var/ossec/bin/ossec-execd
------------------------------------------------ more ------------------------------------------------
the process command showed that loon runs X since 6th Jun 2009.
look at process 2709 by using netstat
[root@www ~]# netstat -anp |grep 2709
tcp 0 0 0.0.0.0:44526 0.0.0.0:* LISTEN 2709/-bash
tcp 0 0 203.114.11.102:51646 194.14.236.50:6667 ESTABLISHED 2709/-bash
udp 0 0 0.0.0.0:54629 0.0.0.0:* 2709/-bash
it is listening my tcp and udp port and established my tcp port with port number 51646
let see what loon doing now
[root@www alex]# lsof -u loon
COMMAND PID USER FD TYPE DEVICE SIZE NODE NAME
x 2709 loon cwd DIR 9,3 4096 17892533 /var/www/html/crew/libraries/x
x 2709 loon rtd DIR 9,0 4096 2 /
x 2709 loon mem REG 9,0 11370676 /lib/libnss_files-2.5.so (path inode=11370543)
x 2709 loon 3u IPv4 37478934 TCP *:44526 (LISTEN)
sshd 24370 loon 3u IPv6 38236234 TCP 203.114.11.102:8897->52.60.in-addr.arpa.tm.net.my:newlixreg (ESTABLISHED)
bash 24371 loon cwd DIR 9,3 4096 17860330 /var/www/html/www.aviocall.com/upload
bash 24371 loon 255u CHR 136,3 5 /dev/pts/3
it is too long. i had cut down most of them, left the important one.
see the red line. see properly.
he using Ipv6 connected to my server ???????????????
and what he want to do over that upload directory?????
let's see upload directory
[root@www www.aviocall.com]# ls -la upload/
total 113672
drwxr-xr-x 6 loon loon 4096 Jun 9 23:01 .
drwxr-xr-x 11 loon loon 4096 Jun 9 19:10 ..
drwxr-xr-x 2 loon loon 4096 May 30 14:32 files
drwxr-xr-x 2 loon loon 4096 May 30 14:33 images
-rw-r--r-- 1 loon loon 111723227 Jun 9 12:56 Manual Patch 090609.exe
-rw-r--r-- 1 loon loon 4521984 Jun 9 23:03 Manual Patch 090609.exe.1
drwxr-xr-x 2 loon loon 4096 May 30 14:33 pdf
drwxr-xr-x 2 loon loon 4096 Jun 4 00:41 programs
[root@www www.aviocall.com]# date
Tue Jun 9 23:03:54 MYT 2009
look, the time of server and the date of file he modified.
he is doing something. well, i dont mind..
i want to monitor him now.
see, what he doing..
top - 23:05:48 up 167 days, 3:45, 4 users, load average: 0.01, 0.00, 0.00
Tasks: 164 total, 2 running, 162 sleeping, 0 stopped, 0 zombie
Cpu(s): 0.1%us, 0.1%sy, 0.0%ni, 99.8%id, 0.0%wa, 0.0%hi, 0.0%si, 0.0%st
Mem: 2066076k total, 1617796k used, 448280k free, 215712k buffers
Swap: 2096376k total, 120k used, 2096256k free, 1118104k cached
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
2709 loon 15 0 8032 4188 1196 S 0.0 0.2 0:01.06 x
10053 loon 15 0 7268 1696 1376 S 0.0 0.1 0:00.09 wget
24370 loon 15 0 9892 1664 1112 S 0.0 0.1 0:00.56 sshd
24371 loon 15 0 4528 1416 1200 S 0.0 0.1 0:00.03 bash
using wget to get something from somewhere.
see what he get from wget
[root@www ~]# ps -afed|grep wget
loon 10053 24371 0 23:01 pts/3 00:00:00 wget http://bayou.asiasoft.net/CABAL/pds/Manual%20Patch%20090609.exe
root 10371 10342 0 23:13 pts/8 00:00:00 grep wget
download CABAL online game's thingy.
Monday, December 8, 2008
simple command for troubleshoot the network applications
1st, netstat
2nd, lsof
From server itself, you can use the below command
1st, netstat
[root@www errs]# netstat -an|grep 3306
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN
note: see the port is opening :P
2nd, lsof
[root@www errs]# lsof -i tcp:3306
COMMAND PID USER FD TYPE DEVICE SIZE NODE NAME
mysqld 7472 mysql 10u IPv4 12294 TCP *:mysql (LISTEN)
see, you can see those port 3306 is used by service, mysqld
and its PID is 7472
then is USER is mysql and etc.
especially lsof, it will tell you which application are bonded with the particular port.
explore lsof more :P you will get more with this command
from client you can try by localhost see whether the firewall is block it or not :P
C:\Documents and Settings\a13x>telnet www.aviocall.com 3306
Connecting To www.aviocall.com...Could not open connection to the host, on port
3306: Connect failed
see, it is failed to connect. i believe is my firewall block it.
Let see the log form server.
Dec 8 17:56:11 www kernel: Shorewall:net2all:DROP:IN=eth0 OUT= MAC=00:1e:68:9a:f6:19:00:13:7f:c4:47:1a:08:00 SRC=118.100.42.9 DST=203.114.11.102 LEN=48 TOS=0x00 PREC=0x00 TTL=113 ID=40540 DF PROTO=TCP SPT=50960 DPT=3306 WINDOW=65535 RES=0x00 SYN URGP=0
Dec 8 17:56:15 www psad: scan detected: 118.100.42.9 -> 203.114.11.102 tcp: [3306] flags: SYN tcp pkts: 1 DL: 1
see the log, the destination port is 3306 :P
that mean my firewall block it :P
so, the conclusion is mysql port 3306 only accessible by localhost or certain IP addresses :P
that's all for this part. Once you know what is the root cause, then only you can perform the troubleshooting.
another way , use sniffer like wireshark or tcpdump to troubleshoot it :P
you can get more :P but i dont plan to teach as im not really good in wireshark and this is dangerous tools for people who have evil mindset :P
Saturday, November 22, 2008
fwknopd - Firewall Knock Operator aka SPA, Single Packet Authentication
I know the fwknop since i brought the bok Linux Firewalls by Michael Rash. He is the guy who created the fwknop, PSAD, fwsnort and etc security tools.
fwknop is a tool use to add the SSH service with specific IP into the iptables' rule and it is just available for 30 seconds to connect to server. Once time exceed, it will remove the rule from iptables, so that no one can connect to server.
For more information , please read the book Linux Firewalls and official website from Michael Rash http://www.cipherdyne.org/fwknop/
Now I have 2 boxes,
Node1 = 192.168.145.41 ( also known as server )
Node2 = 192.168.145.42 ( also known as client )
Node1 has been setup with firewall block the port 22
At, node2, now we do ssh to node1
1st, i scan the node1
[root@node2 ~]# nmap -P0 192.168.145.41 Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2008-11-23 11:56 MYT
Interesting ports on node1 (192.168.145.41): Not shown: 1677 filtered ports
PORT STATE SERVICE
80/tcp open http
113/tcp closed auth
8080/tcp closed http-proxy
MAC Address: 00:0C:29:5E:8B:28 (VMware) Nmap finished: 1 IP address (1 host up) scanned in 22.151 seconds
2nd, i do ssh to node1
[root@node2 ~]# ssh 192.168.145.41
At node1, let see the log
Nov 23 09:04:18 node1 kernel: Shorewall:net2all:DROP:IN=eth0 OUT= MAC=00:0c:29:5e:8b:28:00:0c:29:23:90:aa:08:00 SRC=192.168.145.42 DST=192.168.145.41 LEN=60 TOS=0x00 PREC=0x00 TTL=64 ID=32176 DF PROTO=TCP SPT=44194 DPT=22 WINDOW=5840 RES=0x00 SYN URGP=0
See, my firewall has blocked out the 192.168.145.42.
Node1 :
[root@node1 fwknop]# vi /etc/fwknop/fwknop.conf
EMAIL_ADDRESSES chenghui81@gmail.com;
[root@node1 fwknop]# vi /etc/fwknop/access.conf
SOURCE: ANY;
OPEN_PORTS: tcp/22; ### for ssh (change for access to other services)
KEY: a13xch0ng;
FW_ACCESS_TIMEOUT: 30;
[root@node1 fwknop]# /etc/init.d/fwknop start
Starting the fwknop daemons: [ OK ]
[root@node1 fwknop]# tail -f /var/log/messages
Nov 23 10:03:29 node1 init: Trying to re-exec init
Nov 23 11:33:28 node1 fwknopd: starting fwknopd v1.9.9 (file revision: 1353)
Nov 23 11:33:28 node1 fwknopd: flushing existing iptables fwknop chains
Nov 23 11:33:29 node1 fwknopd: imported access directives (1 SOURCE definitions).
Nov 23 11:33:29 node1 fwknopd: imported previous tracking digests from disk cache: /var/log/fwknop/digest.cache
Nov 23 11:33:29 node1 kernel: device eth0 entered promiscuous mode
Node2, now we do the Single Packet Authentication by using fwknop client
[root@node2 ~]# fwknop -A tcp/22 -a 192.168.145.42 -k 192.168.145.41
[+] Starting fwknop client (SPA mode)...
[+] Enter an encryption key. This key must match a key in the file
/etc/fwknop/access.conf on the remote system.
Encryption Key:
[+] Building encrypted Single Packet Authorization (SPA) message...
[+] Packet fields:
Random data: 2421962114322037
Username: root
Timestamp: 1227411567
Version: 1.9.9
Type: 1 (access mode)
Access: 192.168.145.42,tcp/22
SHA256 digest: uBZSsbkeoAH/pA44IHxLGvHt3rC8F513ry4XCVKimkU
[+] Sending 182 byte message to 192.168.145.41 over udp/62201...
Node1: from the /var/log/messages
Nov 23 11:39:45 node1 kernel: Shorewall:net2all:DROP:IN=eth0 OUT= MAC=00:0c:29:5e:8b:28:00:0c:29:23:90:aa:08:00 SRC=192.168.145.42 DST=192.168.145.41 LEN=210 TOS=0x00 PREC=0x00 TTL=64 ID=43837 DF PROTO=UDP SPT=64210 DPT=62201 LEN=190
Nov 23 11:39:45 node1 fwknopd: received valid Rijndael encrypted packet from: 192.168.145.42, remote user: root, client version: 1.9.9 (SOURCE line num: 26)
Nov 23 11:39:45 node1 fwknopd: add FWKNOP_INPUT 192.168.145.42 -> 0.0.0.0/0(tcp/22) ACCEPT rule 30 sec
(note : see the last line that has added our IP to the iptables in order to let us connect the SSH in 30 seconds)
Node2 : I login the node1 asap
[root@node2 ~]# ssh 192.168.145.41 -l root
The authenticity of host '192.168.145.41 (192.168.145.41)' can't be established.
RSA key fingerprint is be:73:8b:27:48:96:ce:f5:16:7c:c5:0d:81:99:c7:3d.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.145.41' (RSA) to the list of known hosts.
Address 192.168.145.41 maps to node1, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
root@192.168.145.41's password:
Last login: Sun Nov 23 07:04:39 2008 from 192.168.145.1
See the cool things from node1 , /var/log/messages
Nov 23 11:40:56 node1 fwknopd: add FWKNOP_INPUT 192.168.145.42 -> 0.0.0.0/0(tcp/22) ACCEPT rule 30 sec
Nov 23 11:41:28 node1 fwknop(knoptm): removed iptables FWKNOP_INPUT ACCEPT rule for 192.168.145.42 -> 0.0.0.0/0(tcp/22), 30 sec timeout exceeded
See the last 2nd line that told you the iptables has added the new rules to allow IP 192.168.145.42 (aka node2) to login thru port 22 within 30 sec
See the last line that told you the iptables has removed the rules from the iptables which is ip192.168.145.32 port 22 after 30 seconds
Yet, my email, please take a look : -
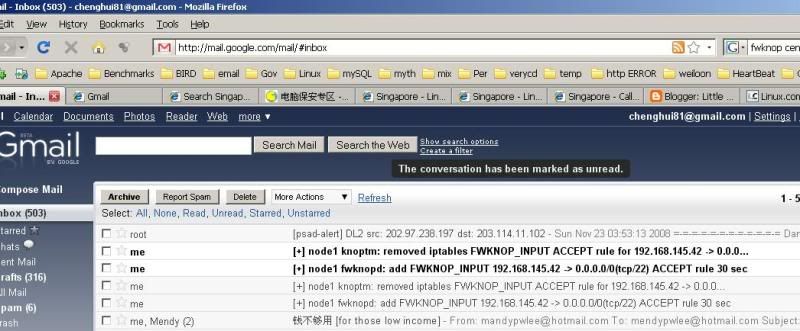
see that 2 unread emails, one is telling you the IP has been added into the iptables and another is telling you the time is exceed and the rule has been removed from iptables
fwknop is designed used to prevent the 0 day exploit..
cause once they scan your server, there is no ssh port opening :P
so, no way they can access into your server thru ssh.
cool is it??
quickly implement into your server to make another security layer for ssh.
PSAD - how it works ???
Nov 22 23:22:36 www kernel: Shorewall:net2all:DROP:IN=eth0 OUT= MAC=00:1e:68:9a:f6:19:00:13:7f:c4:47:1a:08:00 SRC=123.12.89.26 DST=203.114.11.102 LEN=40 TOS=0x00 PREC=0x00 TTL=106 ID=55810 PROTO=TCP SPT=6000 DPT=3389 WINDOW=16384 RES=0x00 SYN URGP=0
Nov 22 23:22:41 www psad: src: 123.12.89.26 signature match: "MISC MS Terminal Server communication attempt" (sid: 100077) tcp port: 3389
Nov 22 23:22:41 www psad: scan detected: 123.12.89.26 -> 203.114.11.102 tcp: [3389] flags: SYN tcp pkts: 1 DL: 2
Nov 22 23:28:03 www kernel: Shorewall:net2all:DROP:IN=eth0 OUT= MAC=00:1e:68:9a:f6:19:00:13:7f:c4:47:1a:08:00 SRC=221.10.240.100 DST=203.114.11.102 LEN=48 TOS=0x00 PREC=0x00 TTL=114 ID=48158 DF PROTO=TCP SPT=4121 DPT=4899 WINDOW=16384 RES=0x00 SYN URGP=0
Nov 22 23:28:07 www psad: src: 221.10.240.100 signature match: "MISC Radmin Default install options attempt" (sid: 100204) tcp port: 4899
Nov 22 23:28:07 www psad: scan detected: 221.10.240.100 -> 203.114.11.102 tcp: [4899] flags: SYN tcp pkts: 1 DL: 2
Nov 22 23:36:02 www kernel: Shorewall:net2all:DROP:IN=eth0 OUT= MAC=00:1e:68:9a:f6:19:00:13:7f:c4:47:1a:08:00 SRC=77.194.196.82 DST=203.114.11.102 LEN=48 TOS=0x00 PREC=0x00 TTL=110 ID=22232 DF PROTO=TCP SPT=4390 DPT=4899 WINDOW=65535 RES=0x00 SYN URGP=0
Nov 22 23:36:07 www psad: src: 77.194.196.82 signature match: "MISC Radmin Default install options attempt" (sid: 100204) tcp port: 4899
Nov 22 23:36:07 www psad: scan detected: 77.194.196.82 -> 203.114.11.102 tcp: [4899] flags: SYN tcp pkts: 1 DL: 2
see this 3 part, once the packet drop by my shorewall ( iptables ), PSAD then perform the job.
Then, It will read the signature if match it will block the IP for certain period
coool, is it?????