I know the fwknop since i brought the bok Linux Firewalls by Michael Rash. He is the guy who created the fwknop, PSAD, fwsnort and etc security tools.
fwknop is a tool use to add the SSH service with specific IP into the iptables' rule and it is just available for 30 seconds to connect to server. Once time exceed, it will remove the rule from iptables, so that no one can connect to server.
For more information , please read the book Linux Firewalls and official website from Michael Rash http://www.cipherdyne.org/fwknop/
Now I have 2 boxes,
Node1 = 192.168.145.41 ( also known as server )
Node2 = 192.168.145.42 ( also known as client )
Node1 has been setup with firewall block the port 22
At, node2, now we do ssh to node1
1st, i scan the node1
[root@node2 ~]# nmap -P0 192.168.145.41 Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2008-11-23 11:56 MYT
Interesting ports on node1 (192.168.145.41): Not shown: 1677 filtered ports
PORT STATE SERVICE
80/tcp open http
113/tcp closed auth
8080/tcp closed http-proxy
MAC Address: 00:0C:29:5E:8B:28 (VMware) Nmap finished: 1 IP address (1 host up) scanned in 22.151 seconds
2nd, i do ssh to node1
[root@node2 ~]# ssh 192.168.145.41
At node1, let see the log
Nov 23 09:04:18 node1 kernel: Shorewall:net2all:DROP:IN=eth0 OUT= MAC=00:0c:29:5e:8b:28:00:0c:29:23:90:aa:08:00 SRC=192.168.145.42 DST=192.168.145.41 LEN=60 TOS=0x00 PREC=0x00 TTL=64 ID=32176 DF PROTO=TCP SPT=44194 DPT=22 WINDOW=5840 RES=0x00 SYN URGP=0
See, my firewall has blocked out the 192.168.145.42.
Node1 :
[root@node1 fwknop]# vi /etc/fwknop/fwknop.conf
EMAIL_ADDRESSES chenghui81@gmail.com;
[root@node1 fwknop]# vi /etc/fwknop/access.conf
SOURCE: ANY;
OPEN_PORTS: tcp/22; ### for ssh (change for access to other services)
KEY: a13xch0ng;
FW_ACCESS_TIMEOUT: 30;
[root@node1 fwknop]# /etc/init.d/fwknop start
Starting the fwknop daemons: [ OK ]
[root@node1 fwknop]# tail -f /var/log/messages
Nov 23 10:03:29 node1 init: Trying to re-exec init
Nov 23 11:33:28 node1 fwknopd: starting fwknopd v1.9.9 (file revision: 1353)
Nov 23 11:33:28 node1 fwknopd: flushing existing iptables fwknop chains
Nov 23 11:33:29 node1 fwknopd: imported access directives (1 SOURCE definitions).
Nov 23 11:33:29 node1 fwknopd: imported previous tracking digests from disk cache: /var/log/fwknop/digest.cache
Nov 23 11:33:29 node1 kernel: device eth0 entered promiscuous mode
Node2, now we do the Single Packet Authentication by using fwknop client
[root@node2 ~]# fwknop -A tcp/22 -a 192.168.145.42 -k 192.168.145.41
[+] Starting fwknop client (SPA mode)...
[+] Enter an encryption key. This key must match a key in the file
/etc/fwknop/access.conf on the remote system.
Encryption Key:
[+] Building encrypted Single Packet Authorization (SPA) message...
[+] Packet fields:
Random data: 2421962114322037
Username: root
Timestamp: 1227411567
Version: 1.9.9
Type: 1 (access mode)
Access: 192.168.145.42,tcp/22
SHA256 digest: uBZSsbkeoAH/pA44IHxLGvHt3rC8F513ry4XCVKimkU
[+] Sending 182 byte message to 192.168.145.41 over udp/62201...
Node1: from the /var/log/messages
Nov 23 11:39:45 node1 kernel: Shorewall:net2all:DROP:IN=eth0 OUT= MAC=00:0c:29:5e:8b:28:00:0c:29:23:90:aa:08:00 SRC=192.168.145.42 DST=192.168.145.41 LEN=210 TOS=0x00 PREC=0x00 TTL=64 ID=43837 DF PROTO=UDP SPT=64210 DPT=62201 LEN=190
Nov 23 11:39:45 node1 fwknopd: received valid Rijndael encrypted packet from: 192.168.145.42, remote user: root, client version: 1.9.9 (SOURCE line num: 26)
Nov 23 11:39:45 node1 fwknopd: add FWKNOP_INPUT 192.168.145.42 -> 0.0.0.0/0(tcp/22) ACCEPT rule 30 sec
(note : see the last line that has added our IP to the iptables in order to let us connect the SSH in 30 seconds)
Node2 : I login the node1 asap
[root@node2 ~]# ssh 192.168.145.41 -l root
The authenticity of host '192.168.145.41 (192.168.145.41)' can't be established.
RSA key fingerprint is be:73:8b:27:48:96:ce:f5:16:7c:c5:0d:81:99:c7:3d.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.145.41' (RSA) to the list of known hosts.
Address 192.168.145.41 maps to node1, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
root@192.168.145.41's password:
Last login: Sun Nov 23 07:04:39 2008 from 192.168.145.1
See the cool things from node1 , /var/log/messages
Nov 23 11:40:56 node1 fwknopd: add FWKNOP_INPUT 192.168.145.42 -> 0.0.0.0/0(tcp/22) ACCEPT rule 30 sec
Nov 23 11:41:28 node1 fwknop(knoptm): removed iptables FWKNOP_INPUT ACCEPT rule for 192.168.145.42 -> 0.0.0.0/0(tcp/22), 30 sec timeout exceeded
See the last 2nd line that told you the iptables has added the new rules to allow IP 192.168.145.42 (aka node2) to login thru port 22 within 30 sec
See the last line that told you the iptables has removed the rules from the iptables which is ip192.168.145.32 port 22 after 30 seconds
Yet, my email, please take a look : -
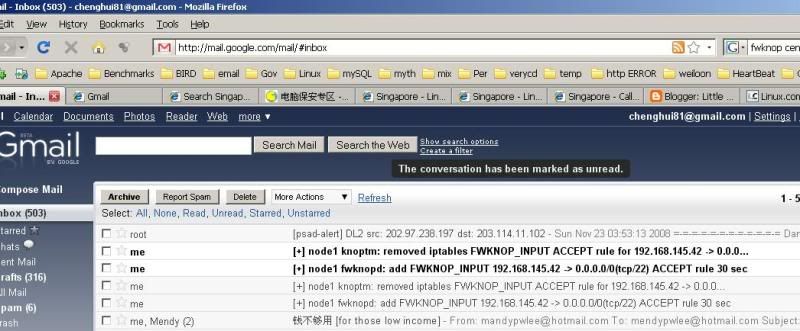
see that 2 unread emails, one is telling you the IP has been added into the iptables and another is telling you the time is exceed and the rule has been removed from iptables
fwknop is designed used to prevent the 0 day exploit..
cause once they scan your server, there is no ssh port opening :P
so, no way they can access into your server thru ssh.
cool is it??
quickly implement into your server to make another security layer for ssh.
4 comments:
yooo linux admin... soon going to be windows admin :D
ahaha..
after 2 years i got both linux and windows server skillset
so i can ask high pay then. :P
Hi Friends,
Great post about configuring fwknop, I was looking for implementing vpn along with fwknop in all the technologies. I was searching on internet and came up with wonderful ebook on implementing vpn technologies through open source (PPTP,L2TP,IPsec,SSL) etc and this book helped me immensely to implement fwknop with vpn so that there are no unwanted connections to any other port. I would recommend everyone to buy the vpn ebook from http://www.ebooksyours.co/how_to_vpn.html
Thanks,
Kandarp
Hi Friends,
Great post about configuring fwknop, I was looking for implementing vpn along with fwknop in all the technologies. I was searching on internet and came up with wonderful ebook on implementing vpn technologies through open source (PPTP,L2TP,IPsec,SSL) etc and this book helped me immensely to implement fwknop with vpn so that there are no unwanted connections to any other port. I would recommend everyone to buy the vpn ebook from http://www.ebooksyours.com/how_to_vpn.html
Thanks,
alok
Post a Comment